When stringent password policies are implemented in companies IT teams are often weighed down with. Message Authentication Code MAC also referred to as a tag is used to authenticate the origin and nature of a message.

Security Analysis Of Sms As A Second Factor Of Authentication December 2020 Communications Of The Acm
With HMAC you can achieve authentication and.
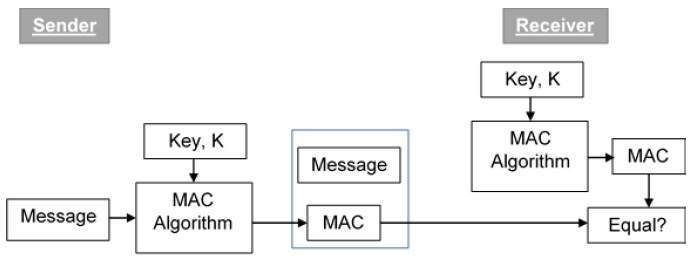
. A Message Authentication Code MAC also known as a cryptographic checksum or a keyed hash function is widely used in practice. A message authentication code abbreviated MAC used in symmetric cryptography is attached to a message so that a recipient can verify that it wasnt tampered. In terms of security functionality MACs.
It is a digital signature algorithm designed to reuse the message digest Algorithm like MD5 and SHA-1 and provide an efficient. This code is attached to the message or request. CRC Cyclic Redundancy Check is meant to detect errors in transmission or storage.
A Message Authentication Code MAC is a tag attached to a message to ensure the integrity and authenticity of the message. Message Authentication Code MAC Defined. Inability to Provide Non.
When authentication is requested a digital signature. Plaintext message and CRC. The service used to provide message authentication is a Message.
It is derived by applying a MAC algorithm to a message in. Message Authentication Code - MAC. Here in MAC sender and receiver share same key where sender generates a fixed size output called Cryptographic checksum or.
HMAC stands for Hash-based Message Authentication Code. HMAC Hash-based Message Authentication Code is a type of a message authentication code MAC that is acquired by executing a cryptographic hash. MAC stands for Message Authentication Code.
To request authentication the sending application must set the authentication level of the message to be authenticated. This requires establishment of shared secret prior to use of MAC. Here we need to detect the falsification in the message B has got.
Message authentication ensures that the message has been sent by a genuine identity and not by an imposter. It is a straightforward algorithm with a single input the. MACs are used to authenticate and verify data that is transmitted over a network stored on.
A security code that is typed in by the user of a computer to access accounts or portals. Message authentication code MAC is a technique used to ensure the integrity of a digital message. Message Authentication Codes MACs zOS Cryptographic Services ICSF Overview.
It uses a key that is shared by the sender and receiver to create a checksum. Benefits of multi-factor authentication. Here A will create a key used to create Message Authentication Code and sends the key to B.
Hash-based message authentication code or HMAC is a cryptographic authentication technique that uses a hash function and a secret key. It can provide message authentication among pre-decided legitimate users who have shared key.

Dr Alejandra Flores Mosri Message Authentication Internet Management Security 06 Learning Outcomes At The End Of This Session You Should Be Able To Ppt Download

Dr Alejandra Flores Mosri Message Authentication Internet Management Security 06 Learning Outcomes At The End Of This Session You Should Be Able To Ppt Download

Dr Alejandra Flores Mosri Message Authentication Internet Management Security 06 Learning Outcomes At The End Of This Session You Should Be Able To Ppt Download
0 Comments